ZK-KYC: A Compliance Deep Dive for Institutional DeFi

ZK-KYC offers a new paradigm for balancing regulatory compliance and user privacy in DeFi.
Introduction
For financial institutions, the digital asset space has long been a frontier of immense opportunity marred by unacceptable risk. The core conflict is stark: the immutable demand for rigorous AML/CFT compliance versus the foundational ethos of privacy and pseudonymity in Decentralized Finance (DeFi). For years, this has created an impasse, relegating institutional involvement to the periphery.
However, a mature and viable architectural solution is now emerging from the cutting edge of cryptography: Zero-Knowledge Know Your Customer (ZK-KYC). This is not merely an incremental improvement; it is a fundamentally new paradigm for identity verification. For compliance officers, risk managers, and strategists, understanding ZK-KYC is a critical component of future-proofing your institution for the next evolution of finance.
Architecting Trust: How ZK-KYC Actually Works
1. The Issuer
A trusted firm performs a rigorous, off-chain KYC check and issues a secure, verifiable credential to the user's digital wallet.
2. The User
The user's wallet generates a zero-knowledge proof to attest they are verified, without revealing any personal data.
3. The Protocol
The DeFi protocol verifies the mathematical proof, not the user's identity, and grants access if the proof is valid.
To truly grasp the elegance of ZK-KYC, we must look beyond the flowchart and witness the carefully choreographed digital ballet it performs. The system's genius lies in its separation of duties, distributing trust across several actors so that no single entity holds all the keys.
The process begins with the Identity Verifier, a regulated and trusted off-chain entity like a specialized CaaS firm. This verifier acts as the guardian of real-world identity, performing the rigorous, traditional KYC and AML checks that institutions require. Once a user is vetted, however, their personal data is not broadcast. Instead, the verifier grants them a cryptographic "seal of approval"—a verifiable credential that is sent to their private digital wallet. This is the only time their full identity is ever exposed, and it happens in a secure, controlled environment.
Now, the User holds this digital passport. When they wish to access a DeFi service, their wallet acts as a privacy shield. It uses the credential to generate a zero-knowledge proof, a cryptographic assertion that says, "I have been verified by a trusted authority and meet the required criteria," without revealing what those criteria or their personal details are. Finally, this proof is presented to the DeFi Protocol. The protocol acts as an impartial, automated bouncer. It doesn't need to know the user's name or age; it only needs to perform a quick mathematical check to confirm the proof is authentic and was issued by a verifier it trusts. If the check passes, the velvet rope lifts and access is granted. This entire interaction creates a secure "air gap," elegantly preserving privacy while immutably proving compliance on-chain.
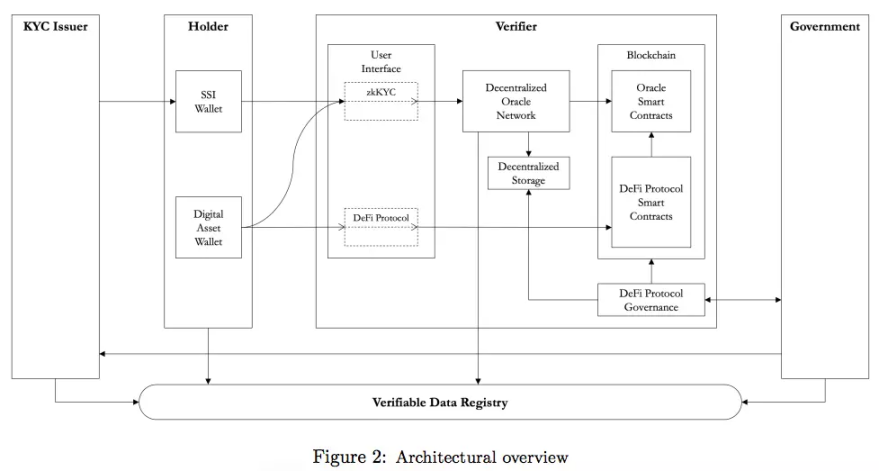
Source: https://eprint.iacr.org/2022/321
A Technical Look: The On-Chain ZK-KYC Flow in Action
Let's move from the conceptual to the concrete. The diagram below illustrates how these pieces fit together in a real-world, multi-chain architecture. This shows how a dedicated identity system can serve a separate "Service Chain" where DeFi applications operate.

An example of a cross-chain ZK-KYC architecture.(https://github.com/hypersign-protocol/zk-kyc-using-ibc)
Here is a step-by-step breakdown of this flow:
- Wallet & DID Creation: The user starts by creating a wallet and a Decentralized Identifier (DID). A DID is a globally unique identifier that the user controls, forming the foundation of their on-chain identity.
- DApp Registration & KYC: The user interacts with a DApp, which directs them to a KYC provider (our "Issuer"). This provider performs the necessary identity verification.
- Credential Issuance: Upon successful verification, the KYC provider issues a Verifiable Credential to the user's wallet. This digital document contains specific attributes (like Age, Country, Name) but is held privately by the user.
- Proof Generation: To access a service, the user's wallet (our "Prover") uses the credential to generate a zk-proof. This proof might attest that "the user is over 18" without revealing their actual birthdate.
- On-Chain Verification & IBC: The zk-proof is submitted to a zk-proof verifier contract on the identity chain (e.g., Hypersign). This contract checks the proof's validity. If valid, it uses the Inter-Blockchain Communication (IBC) protocol to send a simple "True" message to the Service Chain.
- Whitelisting: A Whitelisting Contract on the Service Chain receives the "True" message. It then adds the user's DID or wallet address to an approved list, granting them access to permissioned DeFi applications like a DEX, Airdrop, or LBA contract.
This architecture is powerful because it keeps all Personally Identifiable Information (PII) off the main Service Chain, isolates the verification logic to a specialized identity chain, and enables compliant access across different blockchain ecosystems.
A Paradigm Shift for Compliance Professionals: The Core Benefits
Granular, Composable Compliance
ZK-KYC moves beyond a binary "KYC'd/not-KYC'd" status. It allows for highly specific attestations. A protocol can be configured to require different proofs for different actions, allowing institutions to create tiered access and sophisticated products that precisely match compliance requirements to risk levels.
Drastic Mitigation of Data Breach Risk
Since DeFi protocols never receive or store raw PII, the attack surface for massive data breaches is dramatically reduced. This aligns perfectly with data minimization principles enshrined in regulations like GDPR.
The "Lawful Intercept" Model for Regulation
The KYC Issuer maintains the secure, off-chain link between the user's real-world identity and their on-chain pseudonymous address. This link is protected by stringent legal standards and can only be revealed upon receipt of a valid and properly scoped legal order.
This provides a clear, auditable path for law enforcement without compromising the day-to-day privacy of all other users. It is privacy, not absolute anonymity.
Navigating the Implementation Challenges: A Realistic Outlook
To provide credible counsel, we must acknowledge that the path to widespread ZK-KYC adoption is not a simple plug-and-play solution. It requires clearing several critical hurdles. These are not insurmountable barriers, but realistic challenges that demand careful planning and industry-wide collaboration.
The first and most foundational challenge is the problem of Issuer trust. The entire ecosystem's integrity rests on the reliability of the entities issuing the initial credentials. A single corrupt or incompetent verifier could approve a sanctioned individual, poisoning the well for everyone. This necessitates the creation of a "gold standard"—a robust framework for accrediting, auditing, and holding Issuers accountable, ensuring they all adhere to the highest compliance benchmarks.
Next is the dynamic and complex revocation dilemma. A user's status is not static; they could be added to a sanctions list tomorrow. How do you instantly invalidate their "digital passport" across the entire ecosystem? A system for real-time credential revocation is a non-negotiable security requirement. While technically challenging, this is essential for ensuring the compliance status of the network remains perpetually up-to-date and trustworthy.
Finally, institutions must navigate an evolving regulatory landscape. The technology of ZK-KYC is currently outpacing policy. Regulators worldwide are still learning how to approach such powerful Privacy-Enhancing Technologies. This means early institutional adopters cannot be passive. They must become active pioneers, engaging in dialogue with regulators to demonstrate the technology's capabilities and help write the rulebook for this new frontier, ensuring innovation and compliance can advance hand-in-hand.
The Path Forward: From Theory to Institutional Pilot
The ZK-KYC ecosystem is maturing quickly. For a forward-thinking institution, the time for passive observation is over. The strategic imperative now is to engage.
- Initiate Pilot Programs: Start small. Engage with a CaaS provider and a ZK-KYC technology vendor to build a proof-of-concept.
- Form Internal Working Groups: Bring together experts from compliance, legal, risk, and technology to build institutional knowledge.
- Engage with Regulators: Proactively open dialogues with your regulatory bodies to demonstrate the technology's capabilities.
ZK-KYC represents the most promising framework for building a bridge between traditional finance and decentralized markets. Our role is to help you navigate this new terrain.